
- 151/2022
- High
EG-FinCIRT has detected an Ongoing Phishing Campaign that started to target the Financial Sector in Egypt to deliver a new variant of Snake Keylogger Infostealer.
Snake Keylogger is a modular .NET keylogger stealing sensitive information from a victim’s device, including saved credentials, the victim’s keystrokes, screenshots of the victim’s screen, and clipboard data.
The malware usually is delivered by malicious URLs or docs attached to phishing emails.
The document contains embedded macros to download “rich text format (RTF) files” which hold the malformed objects to extract encrypted shellcode.
Snake Keylogger functionality:
- Snake Keylogger sleeps 21 seconds to bypass sandboxes.
- invokes a function called ‘Constructor()’.which invokes another function ‘Program.List_Types()’, where it downloads the Snake Keylogger module.
- ‘Consturctor()’ function calls ‘ToRc()’ function to RC4 decrypt.
- Load the decrypted DLL module (a .Net DLL file), and enumerates its export functions.
- The decrypted .Net Dll sets Snake Keylogger as an auto-run program and extracts an executable PE file into the memory.
- Executable PE file creates a new child process and executes it.
- Snake Keylogger persistence infects windows by adding it to the ‘Startup’ folder inside the ‘Start Menu ’.
- The Snake Keylogger payload file is fully obfuscated, to protect it from being analyzed.
- The Snake Keylogger calls API SetWindowsHookExA() to register a hook callback function to monitor low-level keyboard input to handle and record the keystrokes.
- It has 4 Timers that execute periodically to send the victim’s keystrokes, screenshots, and clipboard data.
Sample of the phishing emails:
- Sending invoice and payment documents to target business and financial departments.
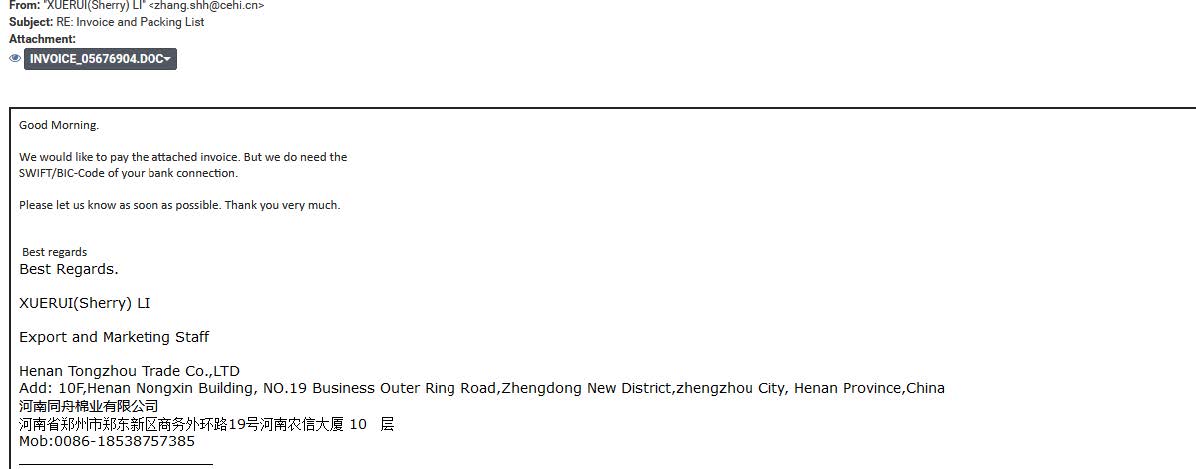
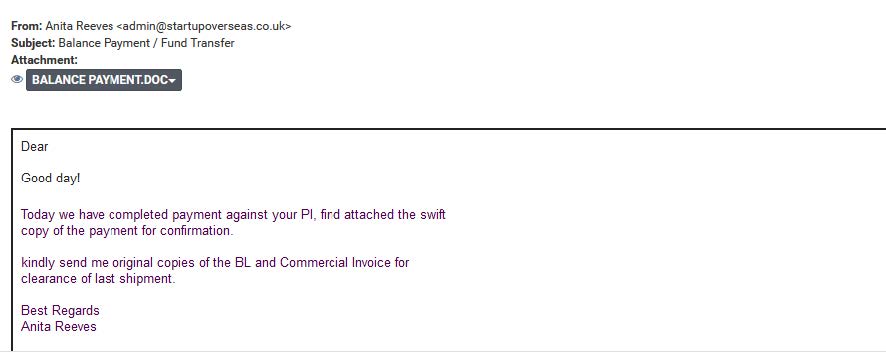
- Sending CVs documents to targeting HR departments.

- It should be highlighted that some of the campaign senders’ domains are spoofed.
Indicators of Compromise
Indicators of compromise will be shared with EG-FinCIRT’s Constituents
Mitigations
- Search for existing signs of the indicated IOCs in your environment.
- Block all IOCs at the firewall, IDS, web gateways, routers, or other perimeter-based devices.
- Users logged into remote access services should have limited privileges for the rest of the corporate network.
- Ensure anti-virus software and associated files are up to date.
- Implement application whitelisting, which only allows systems to execute programs known and permitted by the organization’s security policy.
- Install updates/patches on operating systems, software, and firmware as soon as updates/patches are released.
- Deploy the latest versions of security solutions to all layers of the system, including email, endpoint, web, and network.
