
- 191/2022
- High
FormBook is a data stealer and form grabber that was first advertised on HackForums in early 2016. The malware is associated with APT36, TEMP.Splinter and UNC2589 threat actors which target Financial Services
- FormBook is a self-extracting RAR file that starts an AutoIt loader. The AutoIt loader compiles and runs an AutoIt script. The script decrypts the FormBook payload file, loads it into memory, and executes it.
Malware Characteristics:
- The FormBook malware copies itself to %ProgramFiles% or the %CommonProgramFiles% directories, if the malware runs with elevated privileges. It copies itself to %USERPROFILE%, %APPDATA%, or %TEMP% directories, if the malware runs with normal privileges.
- The malware then iterates over a process listing and calculates a checksum value of the process name. Then it may inject itself into browser processes and explorer.exe.
- The injected code in the hijacked instance of explorer.exe randomly selects and launches (as a suspended process) a built-in Windows executable.
- FormBook sends the following beacon request (controlled by a timer/counter) using HTTP GET with an “id” parameter in the URL.
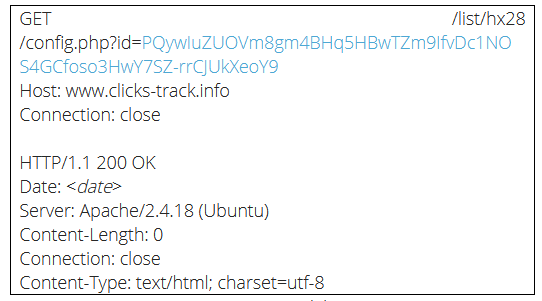
- The malware uses RC4 encryption and Base64 encoding to communicate with the C&C server.
- The malware accepts the following commands from the C&C:
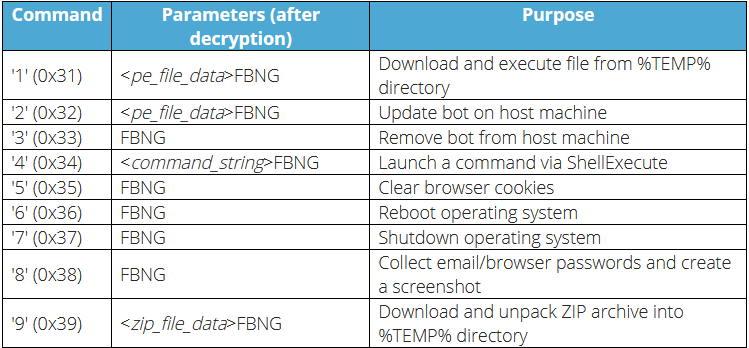
- For persistence, the mentioned malware may write to the registery keys (HKCU | HKLM)\SOFTWARE\Microsoft\Windows\CurrentVersion\Run, or (HKCU | HKLM)\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\Explorer\Run. FormBook malware also has a features to achieve persistance by randomly changes the path, filename, file extension, and the registry key used.
It should be highlighted that mentioned malware has dynamic IOCs that may be changed over time therefore immediate action must be taken.
Vulnerabilities
- CVE-2017-11882
- CVE-2018-0802
Indicator Of Compromise (IOCs)
Indicators of compromise will be shared with EG-FinCIRTs’ constituents.
Mitigations
- Search for existing signs of the indicated IOCs in your environment.
- Block all URL and IP-based IOCs at the organization’s security devices.
- Implement network segmentation such that all machines on your network are not accessible from every other machine.
- If remote access is required, use a VPN with vendor best-practices, multi-factor authentication, password audits, precise access control, and actively monitoring remote accesses.
- Users logged into remote access services should have limited privileges for the rest of the corporate network.
- Administrators should adopt multi-factor authentication and use a separate administrative account from their normal operational account.
- Conduct cybersecurity awareness training for End- users.
- Ensure anti-virus software and associated files are up to date.
- Implement application whitelisting, which only allows systems to execute programs known and permitted by the organization’s security policy.
- Backup your data using different backup destinations, including Tape drives.
- Disable unused remote access/Remote Desktop Protocol (RDP) ports and monitor remote access/RDP logs for any unusual activity.
- Install updates/patches on operating systems, software, and firmware as soon as updates/patches are released.
References
- Egyptian Financial Computing Incident Response Team (EG-FinCIRT)
