
Currently, due to the number of attacks targeting the Active Directory, which are mostly caused by misconfigurations from the domain admin who lacks sufficient knowledge about these threats, it is crucial for the domain admin to understand the risks that threaten active directory environments. Instead of waiting for external third party penetration tests and security assessments, it’s imperative to proactively assess your AD configurations, validate the given permissions and privileges, and pinoint any issues that might be abused by malicious actors.
One possible solution is to have a penetration testing team simulate attacks on the AD to identify existing threats and weaknesses. This practice is commonly performed in many companies. However, it is essential to have a solid understanding of the infrastructure you manage as a system admin. Knowing what you are managing is crucial in protecting it efficiently as a member of the blue team.
To assess the current Active Directory structure, policies, groups, permissions, privileges and accelerate the process, you can use BloodHound.
What’s BloodHound? It’s a tool that can be used to probe and scan the Active Directory and identify weak points. This tool is commonly used by penetration testers to identify misconfigurations, features and permissions that can be abused in the AD to exploit them to get unauthorized access, move laterally, or even reach the domain admin level!
As a system admin, you can utilize this tool to identify misconfigured policies, excessive privileges, unauthorized admins on servers, and potentially abused service accounts that could lead to privilege escalation and compromise the domain admin.
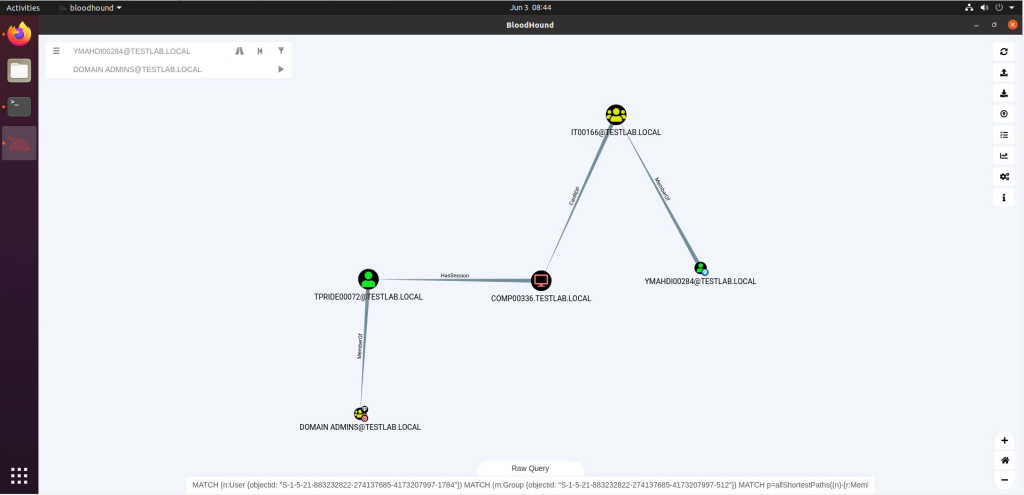
Below, is a very nice figure depicting how the tool pinpoints the path to domain admin privileges. By following the figure, you can see that the user “YMAHDI00284” is a member of the group “IT00166”, any member in this group can RDP into the machine called “COMP00336”, if you RDP into this machine, you will find an active session of the user “TRIDE00072”, who happens to be a domain admin! So if you get your hands on the “YMAHDI00284” or any user of the group “IT00166”, you can theoretically obtain domain admin rights.
“Note that bloodhound shows the things as snap shot in time of when the tool has run. This doesn’t depict real-time results.”
As a system admin, it is recommended to set up a Linux or Microsoft server with a centralized database to run the BloodHound tool. The tool should be executed on a machine joined to the domain with a user having high privilege permissions to query all the configurations, permissions and features in the domain.
It’s also crucial to ensure that the data extracted from BloodHound is not accessible to unauthorized individuals.
If you have an environment SEIM solution in place, it will most likely flag the enumeration scan as an abnormal activity. Therefore, it is essential to ignore such alerts if you are conducting legitimate assessments and reviews.
Conclusion:
Understanding the risks that threaten an AD domain and actively assessing and addressing these weaknesses is crucial for domain administrators. By taking a proactive approach, domain administrators can effectively protect the AD environment and mitigate potential risks between scheduled security assessments.
Ref:
- https://github.com/SpecterOps/BloodHound
- https://www.sans.org/blog/bloodhound-sniffing-out-path-through-windows-domains/
- https://book.hacktricks.xyz/windows-hardening/active-directory-methodology/bloodhound
